Resistance to the Cloud Ain’t Cray
I had a great conversation with one of our creative firms this week about protecting devices. Until recently, they were a little resistant to jump headfirst into the Cloud. To start the conversation, I made one thing very clear: this resistance is/ was completely reasonable. It’s understandable to want to keep high-profile client data in-house. It’s also perfectly sound to want to keep your large unfinished project files stored locally. However, unbeknownst to them, they actually had a bunch of cloud tools in the works already!
Tools that are already (or soon to be) in the Cloud
Here are some common business solutions that are typically in the cloud:
- CRM tools
- HR management
- Project Management
- Time Tracking software
- VoIP
- Mail, Contacts, & Calendar
- Finished Project Files
- Presentations, Documents & Spreadsheets
They recently deployed Insightly (a simple, elegant and secure starter CRM solution to manage contact communication) and were delighted to find the integration with GMail. However, in addition to the Insightly sidebar tool, they were looking to enable the Google Contact Sync and came across this message:
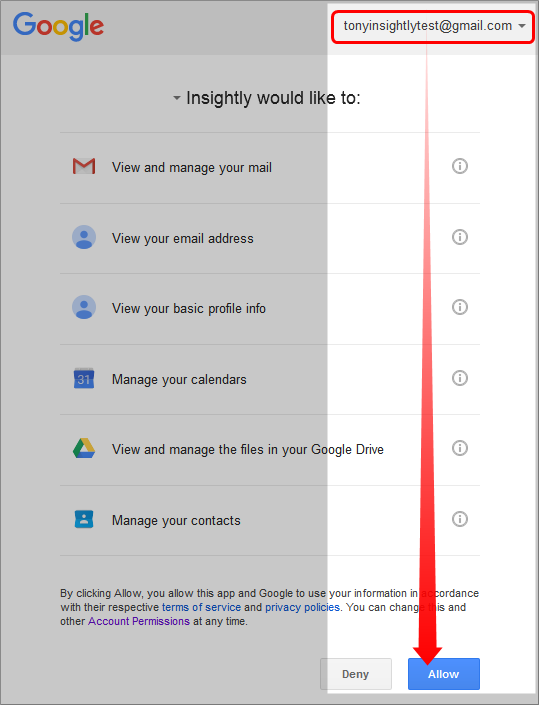
Being fairly new to tools that integrate with G Suite, this message looked pretty threatening. It’s fair to ask, Why do they need access to all of this?! What about my client info? Can everyone at the office see this stuff now?
Rest assured, both Insightly & Google are leveraging incredible security
This got the team thinking about security in a different light. Beforehand, security was mostly about keeping unwanted people entering the building and ensuring the office network was ironclad. Now these tools are “in the Cloud” so, what does that mean?
The same way you wanted to prevent just anyone from entering the office or network unannounced or without permission applies to your mobile devices. You want to add layers of security that prevent access to your iPhones, Laptops, and tablet. Phones get lost. Laptops get left open at coffee shops. Passwords get a little too easy to predict. So what do you do?
The easiest step to protecting your cloud data is through staff education
We talked a lot about 5 simple and (mostly) free ways to protect business data. Protecting your information is a lot easier than you might expect. However, before any tools or security perimeters are put in place, educating the staff on what they are designed to do and why they are so important is the number one first step. Talk to them. Show them these simple steps to protect their devices and, at the very least, you’ll make it a hell of a lot harder to let the bad eggs in.
The 5 Simple and Free Ways to Protect your Business Data
Require more than just a password to sign-in to your stuff:
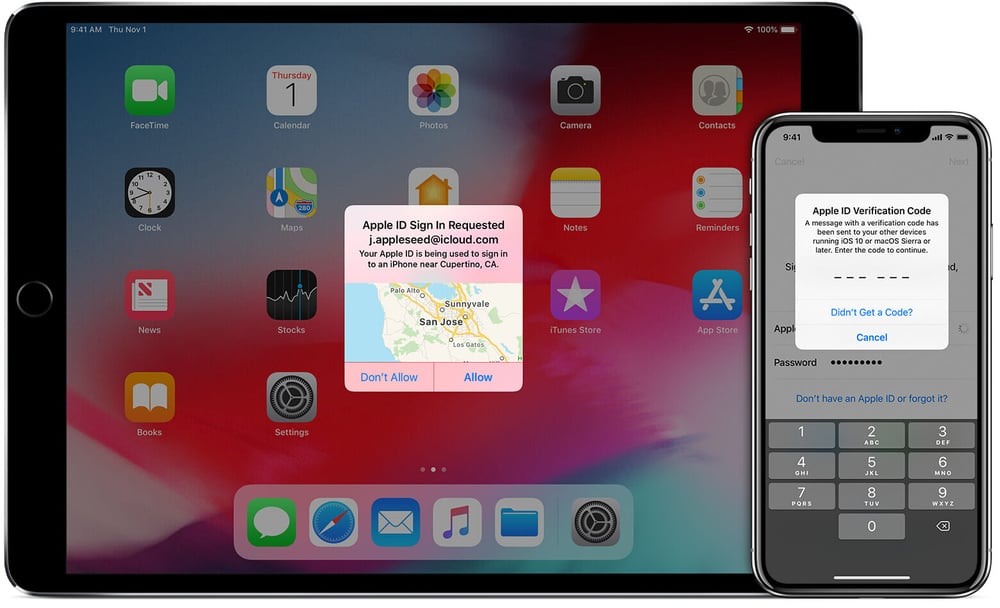
If you’re an iPhone user that recently upgraded to a new device, you probably saw this:
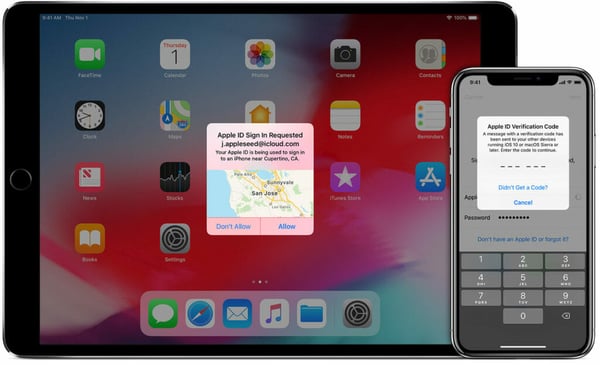
This, in a nutshell, is two-factor authentication -a second form of verification (in addition to your password) to prove your identity.
If your organization uses G Suite, you should really consider enabling two factor authentication and deploying one of the two apps to your team:
Encrypt your machines:
Encryption is a single word used to describe how your machine converts data into a code that prevents unauthorized access. Basically, if your machine gets lost or stolen, encryption makes it very difficult to break into and read your machine without the proper password.
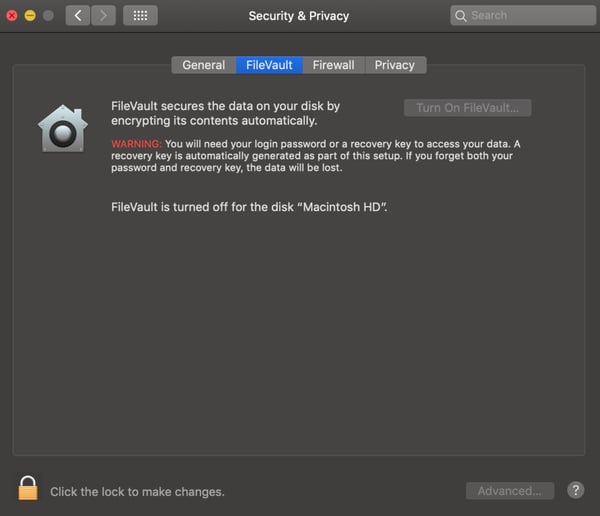
-
- MacBooks offer a tool called FileVault.
- Getting there on a Mac: System Preferences → Security and Privacy → Click on the tab that reads “FileVault”
- On PC with Windows 10 and beyond, you can enable Device Encryption.
- MacBooks offer a tool called FileVault.
Turn on location finders for your phones, tablets, and laptops
This is one of those things you turn on and forget about… until you really, really need it! During our discussion, my favorite quote was “It’s not the device I’m worried about, it’s what’s on them that I worry about.” It was a great point. The cost of replacing a phone or laptop is minuscule to the cost of putting your proprietary data in someone else’s hands. If your device gets lost or stolen these tools will help find them and give you the capability to wipe them remotely.
-
- Find my iPhone, Mac, iPad
- On PC, utilize Device Tracker
- On an Android Device, utilize Find my Device
- Sidebar, any device that is logged into a Google Device can be found via Google’s Tracking software -it even found my Kindle Fire Tablet.
- Sidebar 2: Google is excellent at detecting suspicious logins, check it out
Consider a password manager
Do you or some of your team members still keep sticky notes with passwords on their computer screens? Do you or some of your team members use the same password… for everything? Consider a password manager. You can pick one password that only you know to log into the tool and then it will generate and store a different password for all the stuff you access. Neat right?
Require timed passwords on all devices
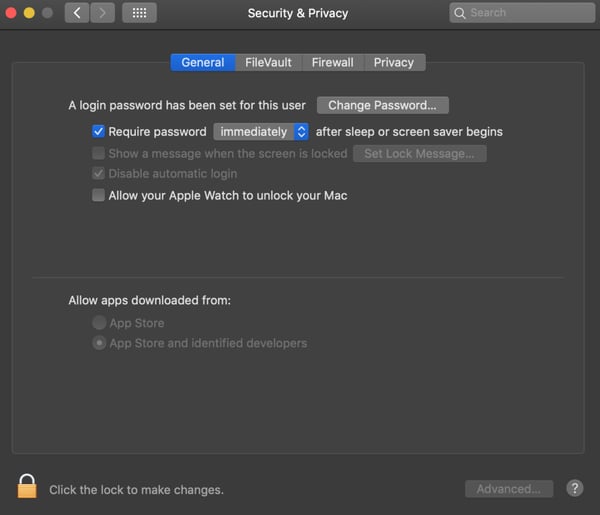
This is pretty self-explanatory but a must. Check your team’s phones and laptops periodically to make sure a passcode (or face/touch ID) is required to open them.
Other fun things that help you secure your stuff:
Ride the Wave Podcast on Phishing
Email best practices (with free cheat sheet to print and hang)
7 Top security questions every business owner should ask
Interested in learning more ways to protect your business data? Schedule a 30-minute IT consultation with our team!
Don't Fall Behind!
Get the latest work-from-home and Humans First® IT tips straight to your inbox.